Our CSIRT service is based on the NIST Cybersecurity Framework (CSF 2.0), focusing on Identify, Protect, Detect, Respond and Recover, surrounded by the Governance. This ensures fast incident handling, minimal disruption, and compliance with NIS2 requirements.

CSIRT: Incident Response Services
Your frontline defense for managing and mitigating cyber incidents.
Specialist team for cybersecurity emergencies
In the event of a security incident, our team of experts is ready for you - we respond quickly, help you limit the damage and assist you restoring your systems.
Crisis management
Forensic analysis
Expertise
Report & Recommendations
Govern
Governance forms the foundation for your resistant cybersecurity management. Here we establish the necessary structures, processes and responsibilities to ensure that cybersecurity is anchored at a strategic level in your company.
Incident Response Plan (IRP)
An Incident Response Plan is a practical, internal playbook that helps your team respond quickly and effectively when a cyber incident happens. It lays out who does what, how to assess the severity, who to notify, and how to keep communication clear, both internally and externally. It also includes legal and compliance guidelines, so actions stay within regulatory lines. Beyond just reacting, it’s about being prepared: having a structured, well-understood approach that reduces confusion, limits damage, and helps the business recover faster with less risk to operations and reputation.

Tabletop Exercise
Our tabletop exercises are grounded in real-world scenarios inspired by actual incidents our team has handled. To ensure the most authentic and valuable experience, the same cybersecurity experts who manage incidents daily are the ones leading these simulations.
These exercises are primarily non-technical and designed to enhance your entire incident response process, from technical teams and communication leads to legal, compliance, executive leadership, and crisis management.
Regularly participating in tabletop exercises is one of the most effective ways to improve your incident handling capabilities. These sessions offer a unique opportunity to apply expert recommendations and identify your own internal improvements in a safe, structured environment.

Get in touch with us
Is your business inadequately protected?
Get in touch with us today to protect your business against cyber threats.
Identify
We identify and analyze all threats and vulnerabilities in your digital infrastructure and assess their potential impact on your business.
Incident Response Readiness
Be Ready Before It Matters Most
Our Incident Response Readiness service helps your organization proactively prepare for cyber incidents by identifying potential gaps and ensuring both your infrastructure and teams are ready to respond efficiently. We focus on two core areas: technical preparedness and security maturity.
On the technical side, we work closely with your team to understand your environment, validate incident response workflows, and identify available tools and data sources that can support investigations. This ensures that when an incident occurs, we already have the context and access needed to act quickly.
At the same time, we assess your security posture using established frameworks such as the CIS Controls and NIST Cybersecurity Framework v2. This provides a clear, actionable view of your strengths and areas that require improvement.
After a short preparation phase, we meet with your team, ideally onsite, to finalize all aspects of readiness. You’ll receive a comprehensive report that includes your current maturity level and prioritized recommendations to strengthen your response capabilities.
Protect
We implement and monitor proactive protection measures that protect your critical systems, data and business processes from known and emerging threats.
Hardening
Our Hardening service focuses on technically assessing a representative baseline of your assets to identify and address vulnerabilities by design, as well as misconfigurations or gaps in best practices. The goal is to reduce your attack surface and strengthen your security posture before an incident occurs.
We review key system components to ensure they're configured securely, this includes checking whether the right data is being logged, verifying secure defaults, and identifying areas where controls can be tightened. Our approach blends industry best practices with our hands-on experience responding to real-world incidents.
This service provides clear, actionable recommendations that help you harden your infrastructure efficiently, improving both detection capabilities and overall resilience against threats.
Get in touch with us
Is your business inadequately protected?
Get in touch with us today to protect your business against cyber threats.
Detect
We monitor your IT environment around the clock and detect security incidents in real time before they can lead to serious business damage.
Threat Intelligence
Our Threat Intelligence service focuses on proactively monitoring the clear, deep, and dark web to identify potential data leaks, compromised assets, or threats targeting your organization. By detecting these early, we help you take swift and appropriate action to reduce risk.
We leverage a combination of our internal intelligence database, fed by both public and private sources, as well as custom threat feeds to support investigations and enrich incident response efforts with relevant context.
In addition, we deliver tailored threat intelligence reports that highlight exposed data, threat actors, and ongoing risks specific to your company. These reports offer actionable insights to help you understand your external exposure and improve your defensive posture.
For a more detailed breakdown of this service and how it can be adapted to your needs, feel free to reach out to our team.

Threat Hunting
Our Threat Hunting service complements existing SOC and Incident Response capabilities by proactively searching for threats that may have evaded detection and are already present within your environment. Our threat hunters formulate hypotheses based on threat intelligence and known attacker behaviors to uncover covert malicious activity.
This approach involves deep analysis of telemetry data, including logs, endpoint activity, forensics artifacts and network traffic, to identify IOCs and adversary tactics, techniques, and procedures (TTPs). It not only strengthens your threat detection and response posture but also helps surface visibility gaps and detection blind spots across your infrastructure.
Additionally, threat hunting engagements serve as realistic training opportunities for your internal teams allowing them to deploy forensic tools and follow investigation workflows as if responding to an active incident.
We also provide detailed threat hunting reports outlining key findings, suspicious behaviours, and evidence of compromise, along with operational recommendation.

Respond
Our specialized Incident Response Team responds immediately to security incidents to limit damage, eliminate attackers and minimize business disruption.
Incident Response
Our dedicated Incident Response Team acts swiftly to contain security incidents and supports you throughout the entire response process.
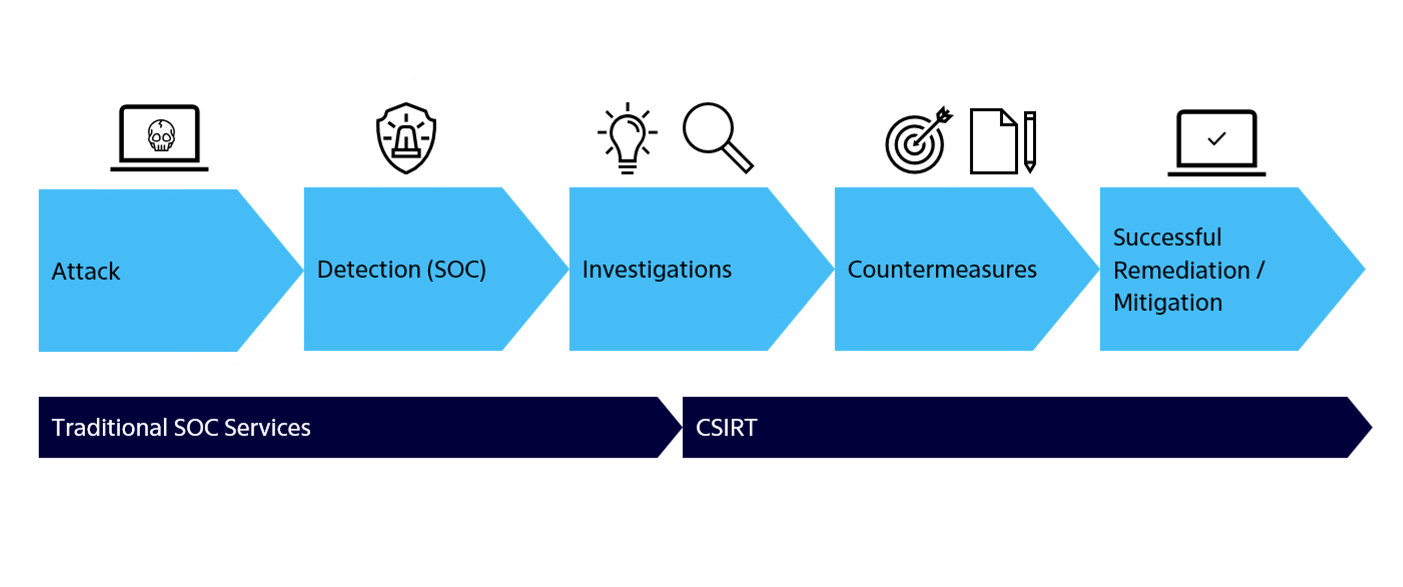
When a cyber incident happens, we always work with two key roles: an Incident Commander and one or more Incident Responders. The Incident Commander takes charge of coordination, making sure everyone’s on the same page, guiding the investigation, and keeping you updated regularly.
Meanwhile, the Incident Responders are the technical experts who jump into the details. They use a carefully built toolkit designed to move fast and get results when every minute counts.
This setup lets us combine strong leadership with hands-on expertise, helping you manage incidents smoothly and minimize their impact.
Get in touch with us
Is your business inadequately protected?
Get in touch with us today to protect your business against cyber threats.
Recover
Help rebuilding infrastructures following security best practices
After an incident is contained, we support you through the recovery phase by providing expert guidance on rebuilding or restoring your infrastructure securely. Whether you’re fully rebuilding or recovering existing systems, we help ensure that security best practices are followed every step of the way.
Our role is to advise on configurations, hardening measures, and controls to reduce vulnerabilities and prevent future incidents, helping you come back stronger and more resilient.
What is the added value of CSIRT?
Our CSIRT (Computer Security and Incident Response Team) is made up of cybersecurity specialists with deep technical expertise and seasoned professionals trained in crisis management.
On the technical side, our team holds top-tier certifications in incident response and digital forensics, enabling them to manage complex investigations while ensuring legal admissibility through proper chain of custody practices. Their extensive hands-on experience spans organizations of all sizes and across various industries.
On the incident management side, our senior experts support you with crisis coordination, legal and compliance aspects, communication strategies, and more. They are specifically trained to guide organizations through high-stakes situations with professionalism and clarity.
Strategic crisis support from our CSIRT team
Executive Statement
"In today’s evolving threat landscape, cyber incidents are inevitable. Swiss Post Cybersecurity's CSIRT ensures you are not facing them alone, delivering swift expert response and guidance when it matters most. We help you with the crisis management as well as with the technical forensics (legal) investigation during emergencies, and also support you to be proactive and reduce the overall risk with different consulting activities."
Greg Divorne
Director of CSIRT
Further services for your protection
Our cyber security specialists have extensive experience that goes far beyond pure incident response. From prevention and continuous monitoring to emergency preparedness and crisis management, we provide holistic protection for your digital company assets.
-
Forensic analysis
-
Proactive incident preparation
-
Holistic cyber crisis management
Forensic analysis
We use digital forensic technologies to secure and seamlessly analyze digital evidence. By using specialized hardware, we ensure that the original evidence remains unchanged and can be used for forensic purposes. This methodical precision enables us to reconstruct complex attack patterns and identify advanced threat actors.
Proactive incident preparation
The most effective incident response begins long before the actual security incident. With our preventive incident assessment, we systematically identify potential bottlenecks and obstacles that could cost valuable time in an emergency.
The result is a customized incident response playbook that is tailored to your company's specific requirements. Our security experts work with you to implement optimized emergency processes that guarantee a coordinated and efficient procedure in the event of an emergency.
Holistic cyber crisis management
Our crisis management team acts as a central interface between the operational CSIRT and your management level. In this way, we create a consistent basis for decision-making and avoid loss of information.
We take over the complete orchestration of crisis management:
Trust CSIRT Networks


FIRST
We are part of the global community of trusted CSIRTs coordinated by FIRST, fostering collaboration and rapid response to security incidents.


Trusted Introducer
Recognized within the TI network, our CSIRT meets established standards for trust and operational readiness in the European CSIRT community.
RFC 2350 and signatures
- RFC 2350 (as pdf)
- RFC 2350 signature (as pdf.sig)
- Public key (as asc file)
Is your company inadequately protected against cyber threats?
We are at your disposal to answer your questions and support you with your concerns regarding Incident Response.
Cyber Blog
On the Cyber Blog you will find the current insights, expert articles, and practical tips on the latest cyber threats and security solutions to enhance your company's digital security.
%20(2880%20x%201440%20px).png)
Free cybersecurity webinars: expand your knowledge and reduce risks

New Microsoft Advance Partner Certifications
Don't Judge a PNG by Its Header: PURELOGS Infostealer Analysis

Insights from the 39C3 Congress in Hamburg

Hacknowledge Lux becomes Swiss Post Cybersecurity Lux SA

Computerworld talked to Daniel Gerber at it-sa

Strenghten your cyber resilience with the Microsoft Envision Workshops

BruCON: Inspiring insight into the world of cybersecurity

Enhancing Physical Security in Investment Companies: A Comprehensive Approach - Part 2

